In the modern hybrid work environment, Microsoft 365 serves as the operational core for countless organizations. This centrality, however, also makes it a prime target for increasingly sophisticated cyber threats. A reactive, “set-it-and-forget-it” security posture is no longer sufficient to protect sensitive data and user identities. This guide provides a detailed roundup of the most critical microsoft 365 security best practices you must implement to build a resilient and proactive defense.
We will move beyond generic advice, offering actionable steps, real-world statistics, and official Microsoft references to fortify your digital fortress. For instance, Microsoft’s own data reveals a crucial insight: enabling multi-factor authentication (MFA) can block over 99.9% of account compromise attacks. This single statistic underscores the immense power of a layered, modern security strategy, which is the central theme of our discussion.
Throughout this comprehensive listicle, we will explore seven equally vital practices that form the pillars of a secure M365 ecosystem. You will learn how to:
By the end of this article, you will have a clear, actionable roadmap for implementing these essential microsoft 365 security best practices, ensuring your data, users, and organization are protected against both current and emerging threats. We’ll provide the specific details needed to move from theory to practical application, safeguarding your collaborative environment.
Implementing robust Microsoft 365 security best practices starts with a foundational layer of protection: Multi-Factor Authentication (MFA). MFA strengthens access security by requiring two or more verification methods to prove a user’s identity. This layered defense means that even if a cybercriminal steals a user’s password, they likely won’t be able to access the account without the second factor.
According to Microsoft, enabling MFA can block over 99.9% of account compromise attacks. It moves security beyond a single point of failure (the password) and introduces a significant barrier for unauthorized access attempts. This is crucial in today’s environment where phishing and credential theft are rampant.

A compromised account is a gateway to your entire digital estate, from sensitive emails in Exchange Online to confidential files in SharePoint and OneDrive. For organizations handling regulated data, like healthcare providers needing HIPAA compliance or financial institutions, MFA is often a mandatory requirement. A key KPI for security teams should be the “MFA adoption rate,” aiming for 100% coverage for all users, especially administrators.
This infographic illustrates the common methods used to satisfy the “something you have” requirement in MFA.
The visualization highlights the diversity of MFA methods, from widely accessible SMS codes to highly secure hardware tokens, allowing organizations to choose the right balance of security and user convenience.
A successful MFA deployment requires careful planning and communication. Rushing a rollout can lead to user friction and helpdesk overload.
Transitioning from a traditional perimeter-based security model to a modern approach requires adopting a Zero Trust architecture. This security framework operates on the principle of “never trust, always verify,” assuming that a breach is inevitable or has already occurred. It treats every access request as originating from an untrusted network, requiring continuous verification for every user, device, application, and data transaction.
In the context of Microsoft 365, Zero Trust means moving beyond the idea of a secure corporate network. Instead, security policies are applied based on the identity of the user, the health of their device, the application they are accessing, and other real-time signals, regardless of their location. Microsoft’s own internal implementation of Zero Trust resulted in a 50% reduction in security incidents while enabling a massive shift to remote work, proving its effectiveness at scale.
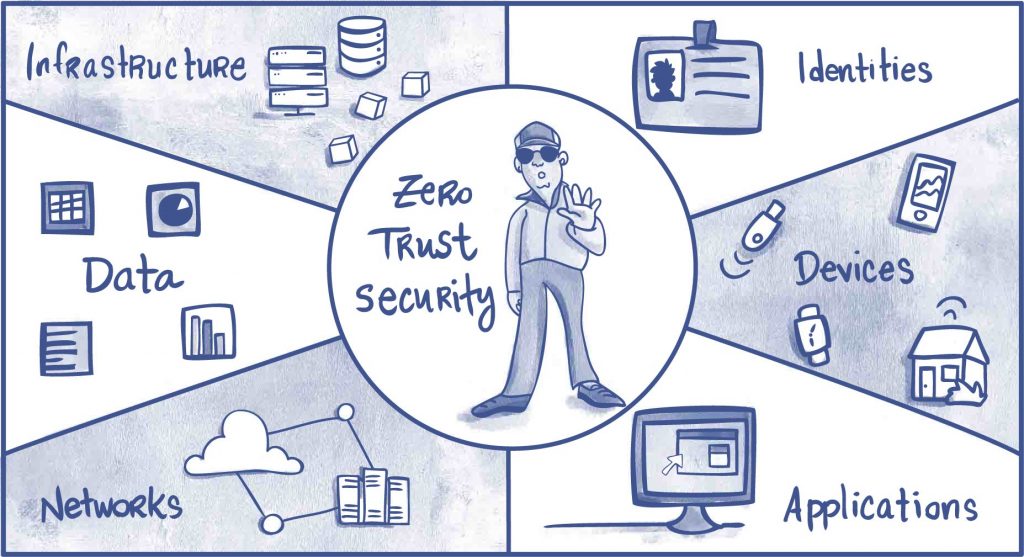
In a cloud-first world, the network perimeter has dissolved. Employees, partners, and contractors access resources from various locations using a mix of corporate and personal devices. A Zero Trust model directly addresses this reality by securing the data and resources themselves. For instance, a global consulting firm successfully used Zero Trust principles to grant contractors secure, VPN-less access to specific SharePoint sites, limiting their access to only what was necessary and continuously verifying their identity and device compliance.
This approach is not just a best practice; it is increasingly a standard. Government agencies are now mandated to adopt Zero Trust architectures to meet federal cybersecurity requirements, highlighting its importance in protecting critical infrastructure and sensitive information.
Implementing Zero Trust is a journey, not a destination. It involves a gradual, phased approach rather than a single deployment.
Beyond standard email filtering, a critical component of modern Microsoft 365 security best practices involves deploying a proactive defense against sophisticated, zero-day threats. Microsoft Defender for Office 365, formerly known as Advanced Threat Protection (ATP), provides this crucial layer. It uses powerful machine learning, real-time threat intelligence, and sandboxing technology to analyze and neutralize advanced attacks like targeted phishing, business email compromise, and polymorphic malware before they can impact your organization.
This advanced security suite goes far beyond traditional signature-based antivirus. It preemptively detonates suspicious attachments in a virtual environment (Safe Attachments) and rewrites URLs to check them against a constantly updated list of malicious sites at the time of click (Safe Links). According to Microsoft, Defender for Office 365 blocks an average of 32 billion email threats per year, demonstrating its massive scale and effectiveness.

Relying solely on default email protection is insufficient against today’s targeted cyberattacks. Defender for Office 365 is designed to stop the threats that standard filters miss, safeguarding your most vulnerable entry point: your users’ inboxes. A key performance indicator (KPI) here is the “mean time to detect” (MTTD) threats; ATP aims to reduce this to near-zero for known and emerging email-based attacks.
The effectiveness is backed by Microsoft’s own data, which shows that organizations using Defender for Office 365 have a significantly lower compromise rate. It acts as a critical backstop, protecting sensitive data within Exchange, SharePoint, and Teams from being compromised via a malicious link or attachment.
A properly configured Defender for Office 365 deployment can dramatically improve your security posture without creating unnecessary friction for users.
Securing user identities is critical, but protecting the data itself is an equally important pillar of Microsoft 365 security best practices. Data Loss Prevention (DLP) policies provide a sophisticated safety net, helping organizations identify, monitor, and automatically protect sensitive information across services like Exchange Online, SharePoint, OneDrive, and Microsoft Teams. DLP prevents the accidental or malicious sharing of confidential data, acting as a digital guardian for your most valuable assets.
Microsoft Purview Data Loss Prevention can identify sensitive items by using deep content analysis, not just by a simple text scan. It uses keyword matches, dictionary matches, regular expressions, and internal functions to detect content that matches your DLP policies. This automated intelligence is crucial for preventing data leaks before they happen.
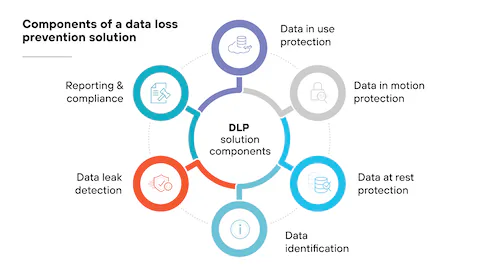
In a world of constant collaboration, the risk of sensitive data exposure is higher than ever. An employee might accidentally email a spreadsheet with customer social security numbers to an external contact or save a document containing proprietary intellectual property to a personal cloud storage account. DLP policies help mitigate these risks automatically, enforcing organizational data handling rules without constant manual oversight.
For instance, a healthcare organization can use DLP to prevent HIPAA violations by creating a policy that blocks any email containing patient health information from being sent outside the company network. A valuable KPI to track is the “number of DLP policy matches” and “override incidents,” which helps gauge user behavior and policy effectiveness.
A well-planned DLP strategy minimizes business disruption while maximizing data protection. A “boil the ocean” approach can create friction, so a phased rollout is recommended.
Another critical component of a comprehensive Microsoft 365 security best practices strategy is implementing Privileged Access Management (PAM). PAM provides granular control over administrative access by granting privileges only when needed, for a limited time. This “just-in-time” (JIT) approach drastically reduces the attack surface associated with standing administrative privileges.
Standing access means that accounts with high-level permissions, like Global Administrator, are always active. If one of these accounts is compromised, the attacker gains persistent, unrestricted access to your entire tenant. PAM mitigates this risk by ensuring privileged roles are inactive until an administrator explicitly requests, justifies, and is approved for temporary elevation.
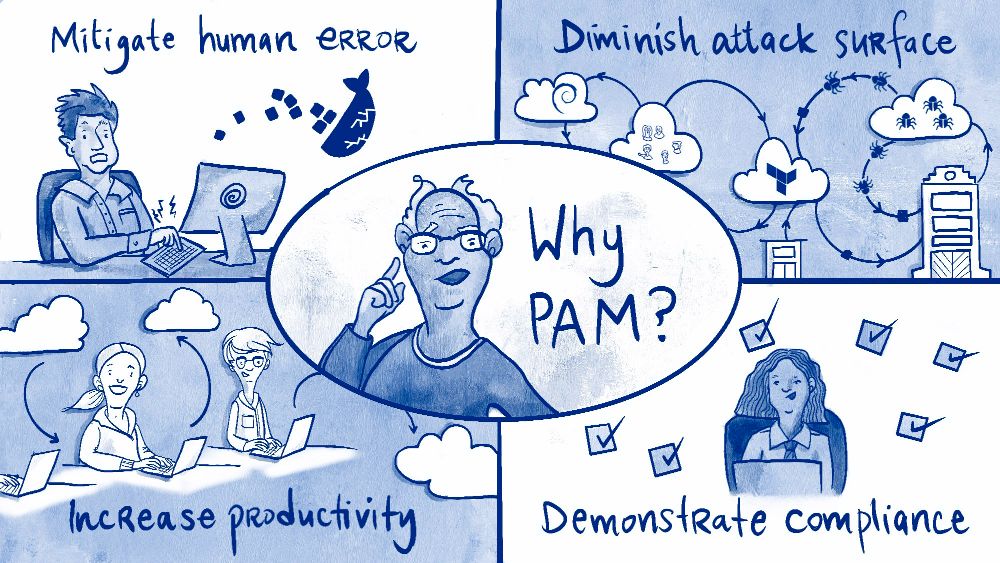
Privileged accounts are the prime targets for sophisticated attackers. A single compromised admin account can lead to catastrophic data breaches, service disruptions, and reputational damage. By enforcing an approval workflow and time-bound access, PAM minimizes the window of opportunity for attackers to exploit these powerful credentials. It also creates a clear audit trail for every privileged action taken.
According to Microsoft, organizations should aim to have fewer than five global administrator accounts to reduce their attack surface. A key KPI for PAM is the “percentage of standing privileged roles converted to JIT-eligible,” with a goal of minimizing standing access as much as possible.
Deploying PAM effectively requires a shift in administrative habits and clear policies. Careful planning ensures a smooth transition to this more secure operational model.
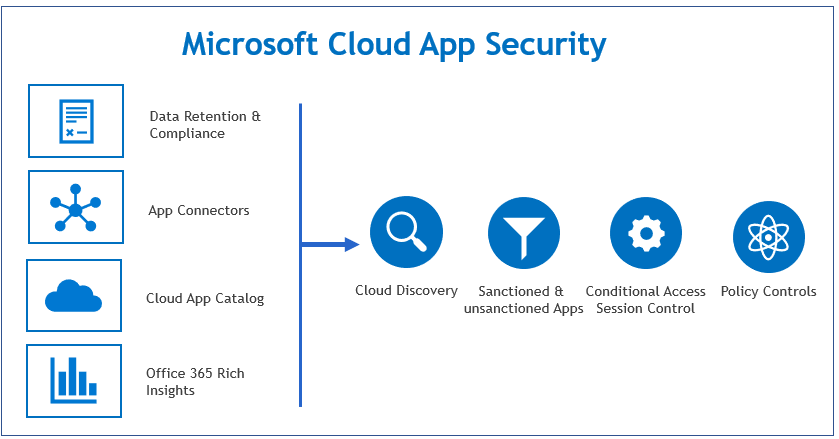
One of the most critical Microsoft 365 security best practices is to harness the power of a Cloud Access Security Broker (CASB). Microsoft Defender for Cloud Apps is Microsoft’s native CASB solution, providing essential visibility, data control, and threat protection for your cloud applications. It acts as a gatekeeper between your users and cloud services, allowing you to monitor activity and enforce granular security policies.
In an era of “shadow IT,” where employees often use unsanctioned cloud apps, Defender for Cloud Apps discovers this usage and assesses the risk of over 31,000 cloud applications. This visibility is the first step toward regaining control over your corporate data as it moves through the cloud ecosystem.
In a world of constant collaboration, the risk of sensitive data exposure is higher than ever. An employee might accidentally email a spreadsheet with customer social security numbers to an external contact or save a document containing proprietary intellectual property to a personal cloud storage account. DLP policies help mitigate these risks automatically, enforcing organizational data handling rules without constant manual oversight.
For instance, a healthcare organization can use DLP to prevent HIPAA violations by creating a policy that blocks any email containing patient health information from being sent outside the company network. A valuable KPI to track is the “number of DLP policy matches” and “override incidents,” which helps gauge user behavior and policy effectiveness.
A well-planned DLP strategy minimizes business disruption while maximizing data protection. A “boil the ocean” approach can create friction, so a phased rollout is recommended.
To achieve a comprehensive and proactive security posture, organizations must move beyond individual alerts to a centralized, intelligent view of their entire digital environment. This is where a Security Information and Event Management (SIEM) solution, like Microsoft Sentinel, becomes a critical component of your Microsoft 365 security best practices. It provides a single pane of glass for threat detection, visibility, and response by collecting and analyzing security data at cloud scale.
Microsoft Sentinel is a cloud-native SIEM that ingests data from across your entire organization, including Microsoft 365 services, Azure, endpoints, and other third-party sources. It uses built-in artificial intelligence to correlate alerts, detect multi-stage attacks, and hunt for threats that might otherwise go unnoticed. This bird’s-eye view transforms security from a reactive, alert-by-alert firefight into a proactive, intelligence-driven operation.
In a complex environment like Microsoft 365, security signals are generated constantly from Exchange Online, SharePoint, Teams, and Azure Active Directory. Without a SIEM, these signals exist in silos, making it nearly impossible to connect the dots of a sophisticated attack. A SIEM aggregates this data, allowing security teams to identify patterns and respond swiftly. According to Microsoft, customers using Sentinel see up to a 90% reduction in alert fatigue and an 80% lower cost compared to legacy SIEMs.
This centralized intelligence is not just for threat hunting; it’s also essential for compliance. Government agencies have used Sentinel to gain unified visibility across multiple M365 tenants, simplifying the process of demonstrating adherence to stringent regulatory requirements.
Deploying a SIEM can seem daunting, but a phased approach focused on high-value data sources can yield immediate benefits. A successful implementation relies on strategic configuration and continuous refinement.
